The last bastion.
Secure access / PAM for your internal SSH, HTTPS, MySQL and Postgres servers with SSO and RBAC.
No client apps needed.
No client
Warpgate directly exposes native SSH, HTTPS, MySQL and Postgres listeners.
DATABASE_URL.No jump hosts
Warpgate handles authentication, and then transparently forwards the connection to the target server, while making a live recording for auditing.
No paid plan
Warpgate is 100% open-source, free and will stay this way forever.
Warpgate is financed through support contracts, and custom-order feature development.
This allows it to escape the otherwise inevitable cycle of stagnation or VC enshittification.
Pro Support →No SaaS bullshit
Warpgate is a single binary (or a Docker image) that you download and run locally on your own hardware.
How is Warpgate different from a jump host / VPN / Teleport?§
| Warpgate | SSH jump host | VPN | Teleport |
|---|---|---|---|
| ✅ Precise 1:1 assignment between users and services | (Usually) full access to the network behind the jump host | (Usually) full access to the network | ✅ Precise 1:1 assignment between users and services |
| ✅ No custom client needed | Jump host config needed | ✅ No custom client needed | Custom client required |
| ✅ 2FA out of the box | 🟡 2FA possible with additional PAM plugins | 🟡 Depends on the provider | ✅ 2FA out of the box |
| ✅ SSO out of the box | 🟡 SSO possible with additional PAM plugins | 🟡 Depends on the provider | Paid |
| ✅ Command-level audit | 🟡 Connection-level audit on the jump host, no secure audit on the target if root access is given | No secure audit on the target if root access is given | ✅ Command-level audit |
| ✅ Full session recording | No secure recording possible on the target if root access is given | No secure recording possible on the target if root access is given | ✅ Full session recording |
| ✅ Non-interactive connections | 🟡 Non-interactive connections are possible if the clients supports jump hosts natively | ✅ Non-interactive connections | Non-interactive connections require using an SSH client wrapper or running a tunnel |
| ✅ Self-hosted, you own the data | ✅ Self-hosted, you own the data | 🟡 Depends on the provider | SaaS |
How does all this work?
You download and run a single binary or a Docker container:
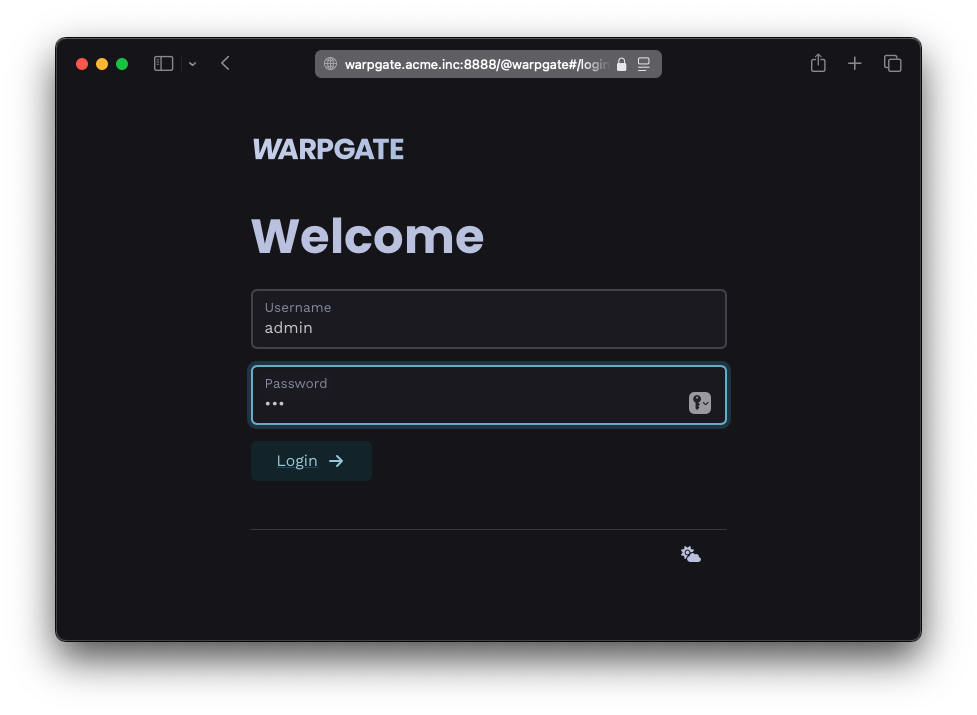
You add your services:
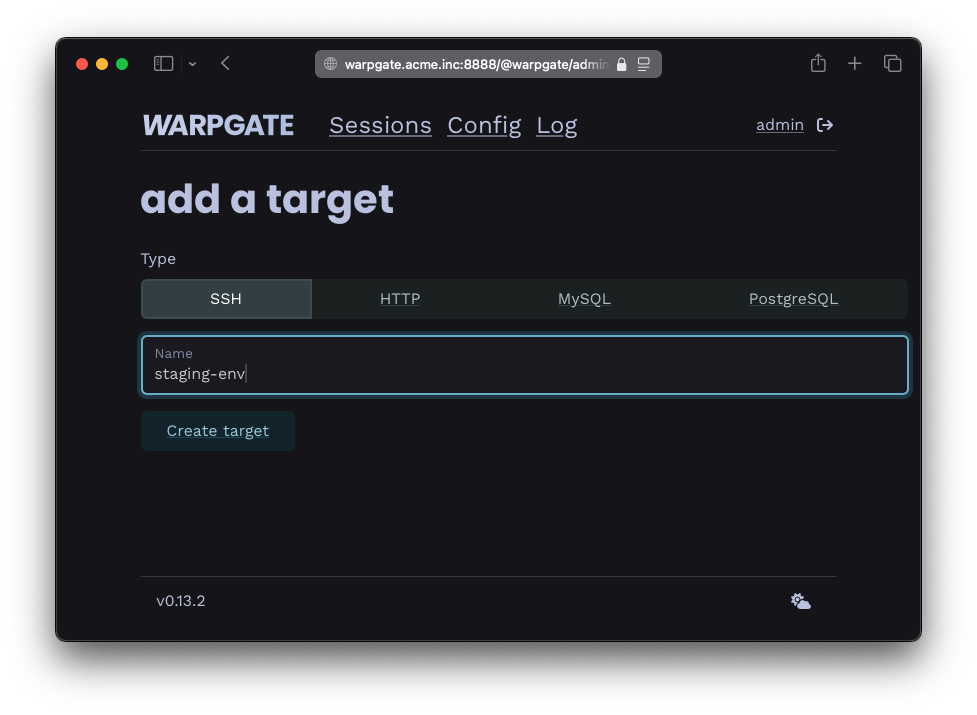
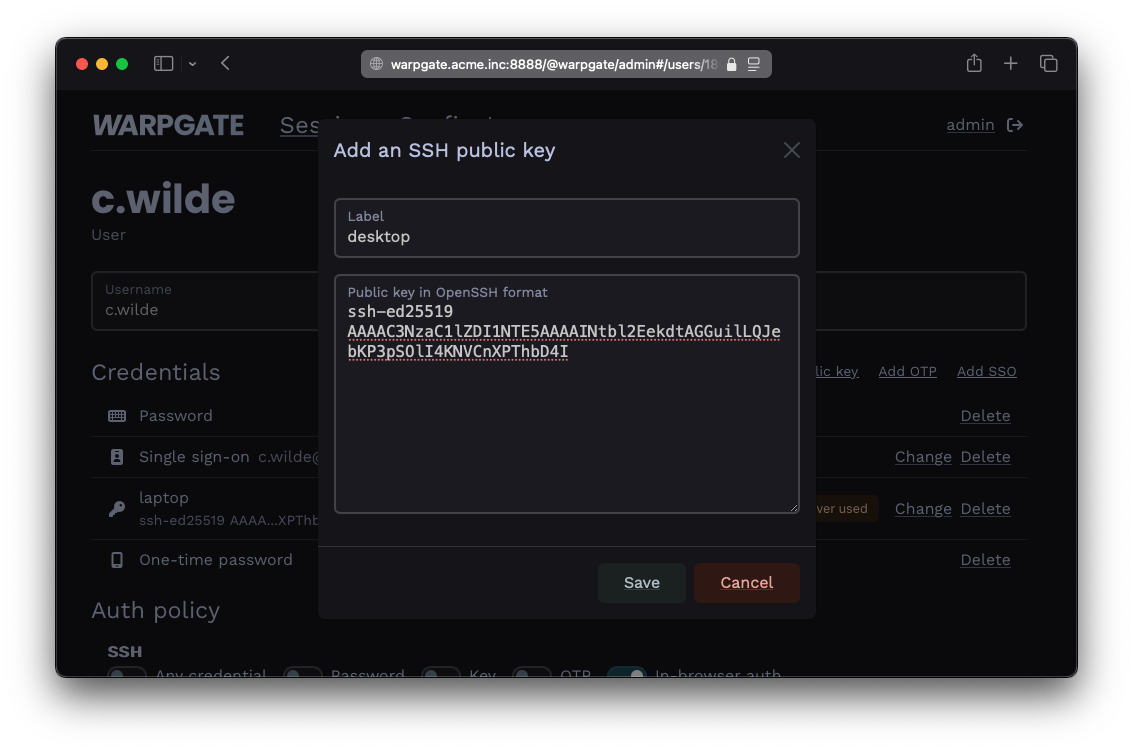
You add your users and decide who can access what: (OIDC SSO supported)
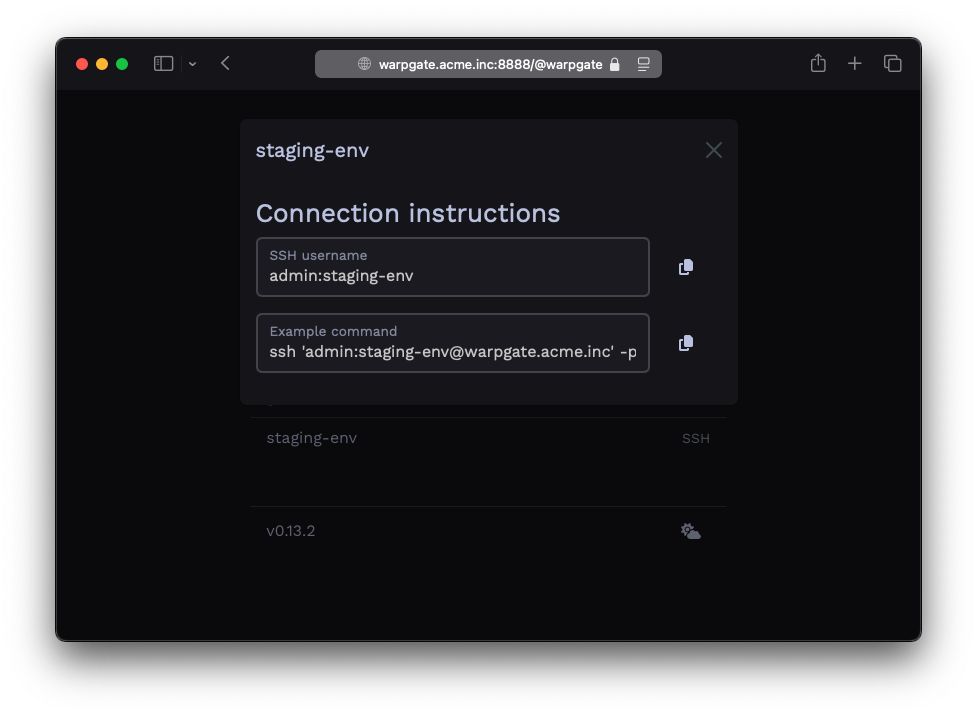
Your users get a specially formatted username to connect to targets:
$ ssh c.wilde:staging-env@warpgate.acme.inc Warpgate Selected target: staging-env Warpgate Host key (ssh-ed25519): AAAAC3[...] ✓ Warpgate connected root@staging-env ~ $
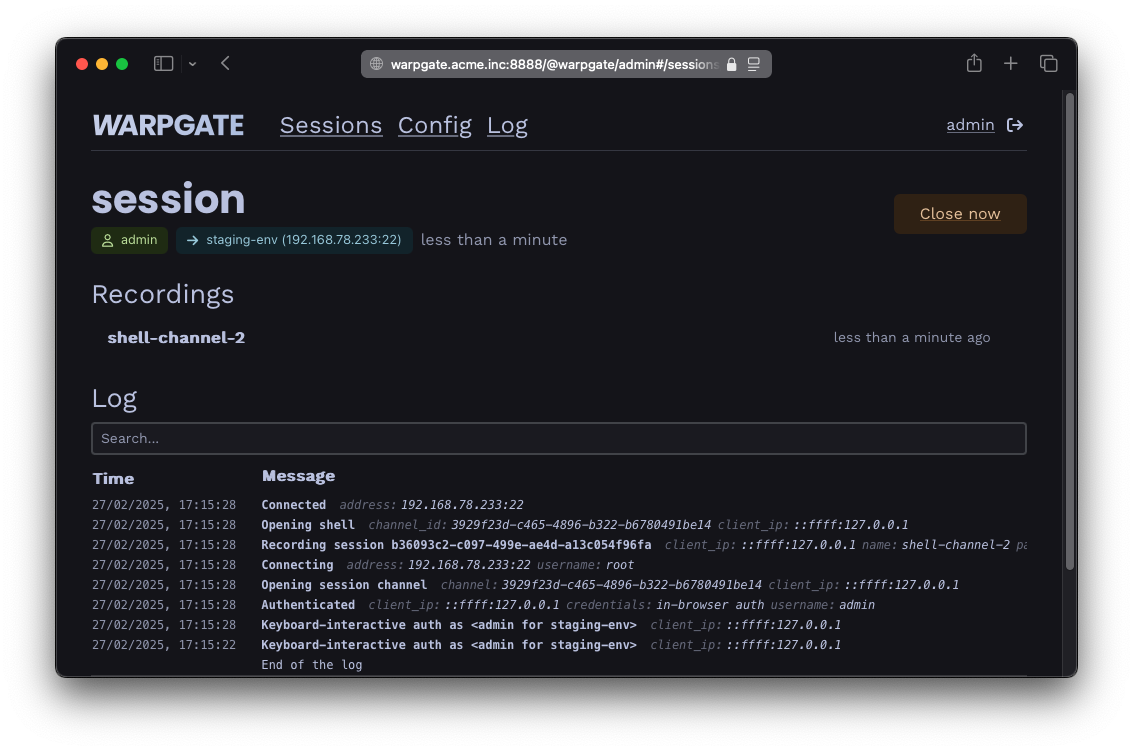
You get audit and observability:
And they get a web interface with instructions so you don't have to keep explaining it:
Sounds good?
Read the docs